Threats catalogs
There is a lot of discussion in the professional community about risk assessment methodologies. At the same time, much less attention is paid to a more powerful indicator of the maturity of the process – the process of building threats catalogs.
Let us turn to a typical assessment process:
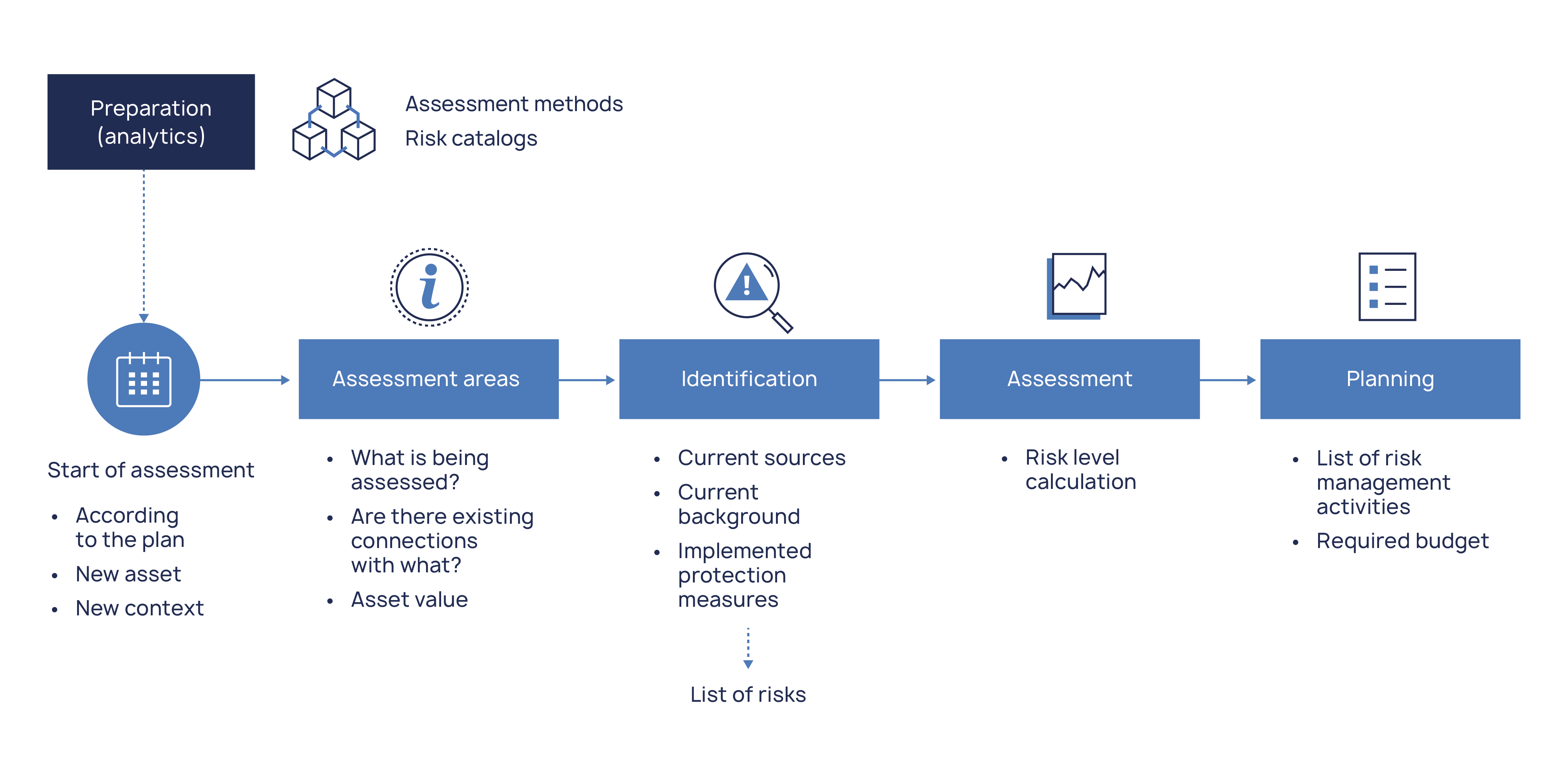
After a one-time event – the preparation of methodological materials – the assessment cycle begins on a schedule or trigger. The first step is to determine the assessment areas, a step that depends largely on the completeness of the data on the resource-service model. As with audits, it is important here to see the connections between tangible and intangible assets.
The value of the asset, the most difficult step in terms of assessment, was discussed earlier.
The next step, i.e. identification, is the formation of a list of risks for further assessment. And it is this step that often becomes a stumbling block for inexperienced organizations.







