20/07/2023

Threats catalogs
There is a lot of discussion in the professional community about risk assessment methodologies. At the same time, much less attention is paid to a more powerful indicator of the maturity of the process – the process of building threats catalogs.
Let us turn to a typical assessment process:
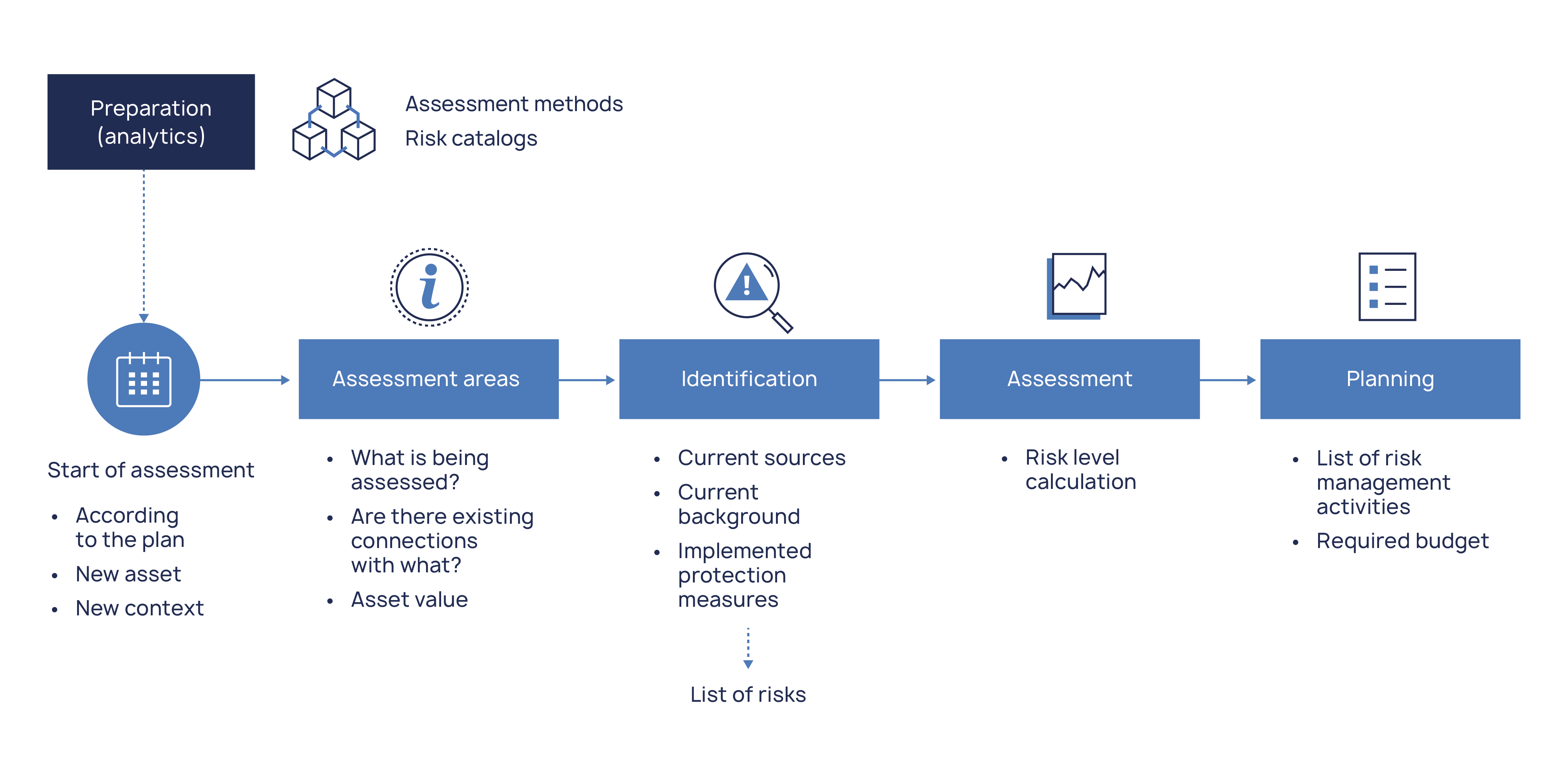
After a one-time event – the preparation of methodological materials – the assessment cycle begins on a schedule or trigger. The first step is to determine the assessment areas, a step that depends largely on the completeness of the data on the resource-service model. As with audits, it is important here to see the connections between tangible and intangible assets.
The value of the asset, the most difficult step in terms of assessment, was discussed earlier.
The next step, i.e. identification, is the formation of a list of risks for further assessment. And it is this step that often becomes a stumbling block for inexperienced organizations.
Often in the first iterations of the process, this step is implemented creatively: experts analyze the asset on the go, during each assessment, and make a list of possible threats. If resources allow, sources and other risk factors are included in the list. As a result, this approach takes a tremendous amount of effort from the experts.
That is why the accumulated experience almost immediately leads to the appearance of threats catalogs – complex directories containing a list of possible threats in an organization. Gradually, the list of threats is supplemented with links to possible sources and other risk factors.
Compiling a threats catalog is a very complex task that requires a responsible approach to the organization’s CS analysis and accumulated data. The situation is complicated by the fact that generally accepted catalogs do not exist because of the great differences in the internal and external contexts of different organizations.
Once catalogs are in place, the “identification” phase is transformed – the main resource is thrown into catalog filtering and selecting relevant risks. Experts no longer waste energy on formulating but still have to manually go through vast amounts of information. The stage is often split into two parts – the selection of threats and the “adaptation” (secondary filtering) of the resulting list.
In contrast to the assessment itself, identification is a step that can be poorly automated with spreadsheets. Semi-manual maintenance saves the day, as long as the number of items goes to a couple of dozens. However, pretty quickly, tables grow to 200+ rows and get filled with macros. The people who used to maintain them get dismissed, and tables begin to slow down rather than simplify the process.
The organization’s threats catalog is a mirror of the experience accumulated by the experts. It inevitably grows in size and complexity – and gradually begins to demand the same from the assessment methodology. Adequately managing such a large catalog forces organizations to work on the maturity of the risk assessment process, otherwise, the process buries them under its complexity.
Speaking about the realization of this process by means of the SGRC system, it is important to note that SGRC removes an enormous amount of manual work from experts, allowing them to free up valuable resources for the analysis of the already prepared list of risks for further processing. Moreover, they take upon themselves the work with historical data, which plays a great role in the assessment, and provide a convenient interface for reference book storage.
Thus, the following advantages of cataloging in SGRC systems can be highlighted:
– Easy navigation in the links between threats and threat factors makes it easy to update catalogs.
– Automatic selection of risks from catalogs frees experts from monotonous manual labor.
– Relevant risk factor questionnaires make identification more objective and less biased – it is harder for experts to adjust results when they do not know where their answers might lead.
– It is easier for experts to work with catalogs, and they can apply more progressive approaches to finding threats, for example – to accumulate experience, including on risk scenarios.
In addition, vendors with deep expertise often have their own threats catalogs and share them with customers, allowing to immediately proceed to a healthy process formation.
