
Today we’re going to tell you about the analytical features of Defensys SENSE – the core functional part of this security analytics platform which main aim is to detect security violations in the infrastructure, different anomalies, suspicious activity and to do the dynamic security scoring of all the objects related to your logs.
Defensys SENSE provides a comprehensive approach for the security events analysis when it studies objects (and similar groups of objects) behaviors, forms normal behavior patterns and detects suspicious activities when they don’t match these patterns.
This qualitative analysis is performed by using 2 types of instruments: simple rules and programmatic experts.
Simple rules
Simple rules is a basic mean to analyze security events and its main feature is a very easy tuning.
Information systems analysts can quickly tune the current rules of create their own ones. When you create a new rule it’s enough to just add criteria for events filtering and as a result all the found events will be marked as suspicious and related observation objects will collect some new number of threat points. Defensys works with the following observation objects: hosts, accounts and users. The overall threat points are aggregated for all the objects that come from logs.
Scoring is the mean to evaluate objects’ anomalies and the potential impact that can occur if this anomaly will become a threat.
This scoring system is tuned under the needs of every company where SENSE is installed and it helps the system to add more threat points when critical for a particular company anomalies are detected. This way analysts can focus on the most important objects for their company in the system.
Meanwhile if there is an objective to receive an alert without scoring rules for objects you can tune such alert rule to notify when a simple rule finds an event. That’s the way to receive some required alerts without their relations with objects.
When you tune a rule you can switch it on/off or even delete depending on the current needs. SENSE analytical platform has the capability to store events. And if some of the rules were switched off the system will recommend you to launch a retro analysis when you try to enable it for not to lose some of the anomalies.
The system has an export/import feature for simple rules to rapidly transfer them between different instances and it significantly reduces the time spent by analysts on this routine with the rules.
Programmatic experts
Programmatic experts are special algorhytms that use statistic analysis and machine learning methods to detect particular anomalies in security events flow. Unlike simple rules programmatic experts have more complicated logic for decision making. Initially programmatic experts study observation objects behaviors and detect anomalies while simple rules detect only events and violation indicators that were preset.
The current version of SENSE has the following experts.
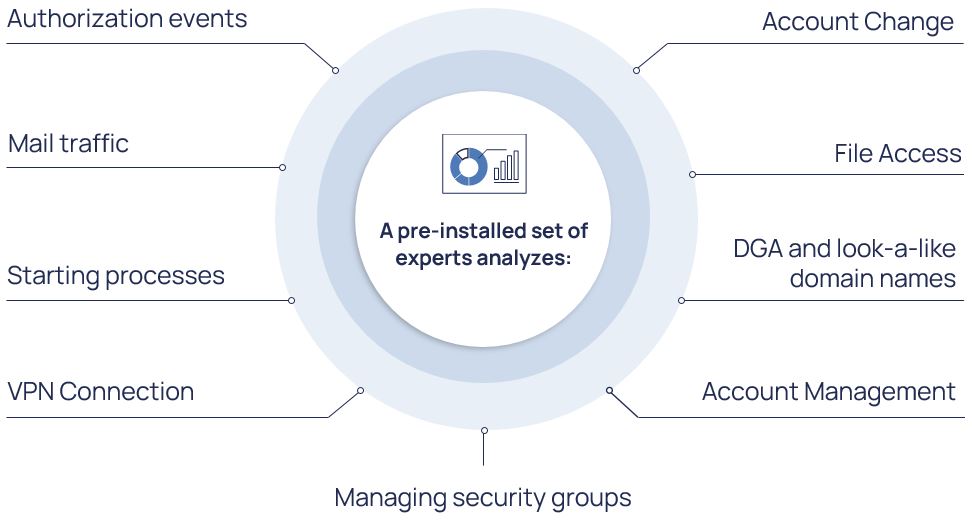
These experts can detect more than 50 different anomalies that recognize popular attack vectors according to the MITRE ATT&ACK matrix.
Some of the experts contain behavioral models that can create behavioral pattern for each observation object using retro data.
This process of building the behavioral pattern is called studying.
Than these exact patterns and profiles will be used by the expert for comparing object’s activities. This way actions that are not usual for the object’s built pattern are considered as anomalies by the SENSE and as a result such objects collect new threat points to the overall score.
Also experts use signature search methods and methods of “studying with the teacher” for the detection of specific threats. Example of such experts can be DGA and look-a-like that detect “suspicious sender name”. These experts don’t need to study, they are ready to do the analytics just after the installation.
All the object’s anomaly actions after simple rules and experts do their job are represented in the form of threat points and it makes much more easy way to work in a huge amount of events and do the investigation ASAP.
When using both simple rules and programmatic experts analysts form cybersecurity departments can detect attacks that were not detected by other security tools previously. And these people can dynamically assess risks related to all the registered cyber incidents for setting the proper priorities when doing the incident response.
The Defensys SENSE uses an agile approach for utilizing analytical tools: simple rules and programmatic experts adapt automatically when data sources alter. This way when there are new log sources and data models coming to the system there is no need to retune the system.
This article describes only a part of all the SENSE capabilities. You can study all the features with its details on the product’s page.
