
An important role in data handling for Threat Intelligence plays knowledge for understanding of threats’ context and their interconnections to certain tactics or hacker groups. Therefore, the lack of necessary data leads to an incomplete understanding of different cybercriminals’ approaches for their attacks. Companies need context regarding indicators, interconnections between threats and attacks to easily identify more dangerous threats and prioritize the ways to eliminate them.
The Defensys TIP is integrated with the knowledge base MITRE ATT&CK®. Thanks to this, users can apply the information regarding hackers’ techniques and tactics to determine the possible ways of threats’ development and preventive protection of information infrastructure.
Threat Intelligence with MITRE ATT&CK®
MITRE ATT&CK® (Adversarial Tactics, Techniques & Common Knowledge) is the knowledge base, that describes and classifies attackers’ behavior based on the analysis of their actions during real attacks. This is a structured list of known behavior types, that are united according to tactics and techniques and grouped in several matrices.
The matrix ATT&CK for Enterprise was created to classify attacks on corporate infrastructure and includes techniques and tactics for Windows, Linux and/or MacOS operating systems. The matrix also describes behavior types of cyber criminals while attacks against corporate systems. Analysis of the mentioned techniques helps to identify weaknesses in the existing security system and take preventive actions.
MITRE ATT&CK® is a tool for attacks’ analyzation and classification, that contributes to effectively response on cyber threats. One of the key advantages of the knowledge base is the standard description of malicious entities, behavior and used tools. That makes MITRE similar to a dictionary, that each user can refer to in a controversial situation.
For analysis of incidents or threats reports for tactics, techniques and procedures (TTP) you can use information from the MITRE ATT&CK®. Matching of observed actions to those described in the knowledge database simplifies incident attributing to a particular group or attack type.
Besides, users can develop scenarios of potential attacks and threats for threat response “drills” based on the information taken from the MITRE base.
MITRE ATT&CK® application for the Defensys TIP
Integration of the Defensys TIP with the MITRE ATT&CK® knowledge base enables users to receive more context about malware, threat actors and their techniques directly from the platform’s interface in the “Threats” section. With the knowledge of used tools, you can build effective defense for the organization.
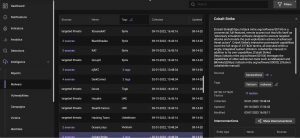
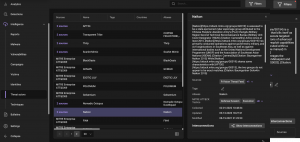
Threat entity cards contain all the information from the MITRE ATT&CK®: entities’ descriptions, linked sub-techniques, links to information resources, that present cases where certain techniques were used by attackers, and recommendations for their detection.
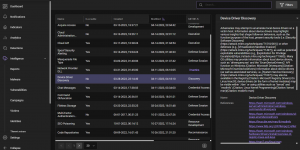
In addition, the Defensys TIP can link tactics from the MITRE ATT&CK® to final indicators of compromise (IoCs), if such interconnections were identified during analysis. These interconnections are demonstrably reflected in the indicator card, enabling TI analysts to assess attack stages more quickly, choose incident response tactics, and prioritize actions.
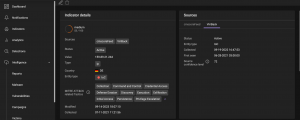
Users can also find interconnections of techniques and IoCs in the relationship graph. For example, you can see which groups use similar techniques and what malware they choose.
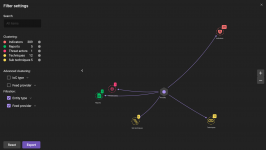
When IoCs are detected within the infrastructure through integration with a SIEM system, users can get a fuller context of what is happening and understand what needs to be countered. This allows the most effective action to be taken in response to a detected threat.
Thus, with knowledge of attacker approaches, interconnections between infrastructure events, IoCs and tactics, integrated in the Defensys TIP, platform users can get a complete picture of cybercriminal behavior and the possible development of the attack.
ATT&CK’s integration with the Defensys TIP helps to optimize analysts’ work with the MITRE matrix, focus only on the knowledge that has a relation to a specific indicator, effectively prioritize threats, and save valuable time needed for a threat prevention.
You can learn more about other features of the Defensys TIP platform on the product page. You can submit a request for system demonstration on our website.
